Phishing Attacks on FileMaker Platform Files
Phishing Attacks on FileMaker Platform Files
Recently I made reference in several venues to an article that described a sophisticated and interesting exploit to steal iOS credentials from a stolen Apple iPhone. You can read the full article here:
https://hackernoon.com/this-is-what-apple-should-tell-you-when-you-lose-your-iphone-8f07cf73cf82
The core element of the article was that when the owner discovered the theft that he activated “…all the ‘send me email when the phone returns online’ checkboxes….” Some eleven days later, the owner received an email and a SMS that the phone had been found. All the owner needed to do was to log-in to iCloud to see the location where the phone was.
The only problem was that the message was a spoof of iCloud. It was a classic phishing attack designed to capture the owner’s credentials.
This episode brought back to mind an example of a similar style ruse that an attacker could possibly perpetrate against a FileMaker Pro file. I showed a brief example of this during my presentation at the 2015 DevCon.
In such an attack a Threat Agent might trick a user into believing that he or she had entered credentials incorrectly, most likely due to a mistyping. Such so-called “fat-finger” errors occur all the time. FileMaker Pro presents the user with a dialog box advising of the error, and it asks the user to please try again.
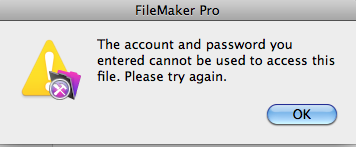
The user then clicks the OK button and enters the credentials again. This time, the credentials work, and the user proceeds to go about his or her business in the file.
But there was no credentials failure the first time around. The user had entered the correct credentials. One of these dialogs is real; the other is not, and it is the beginning of a phishing attack. The purpose is to trick the user into entering the credentials a second time, so that they may be captured in clear text and later used for nefarious purposes.
That subsequent credentials entry box as shown below is a bit harder to spoof than is the error message. But when an Attacker can do that, this exploit likely will trick many users and possibly even some developers. Remember, it does not have to be perfect. It only has to be good enough to trick the user.
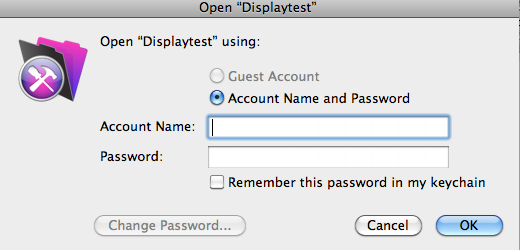
This is but another reason developers and FileMaker Server Administrators must carefully review their systems to be sure that no vectors are open that could facilitate such an attack. Here are some such vectors:
- Guest Account enabled and attached to the [Full Access] Privilege Set
- A [Full Access] Account with no password
- A [Full Access] Account with the password stored using the File Options “Log In Using” feature.
By default, FileMaker® Server 15 will not open such files for hosting. Administrators can authorize the hosting of such files by unchecking an option in the Server Admin Console. I strongly recommend that they not do so. Additionally, earlier versions of FileMaker Server will host such files automatically. Carefully audit those server for the presence of such files.
Steven H. Blackwell





Recommended Comments